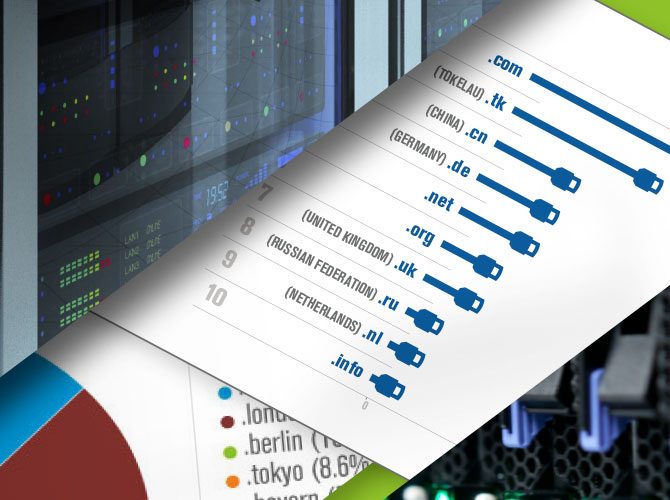
If you are trying to communicate anonymously on the internet using Tor, this paper may be an important read for you. Anonymity and privacy are at the core of what the Tor project promises its users. Short for The Onion Router, Tor provides individuals with a mechanism to communicate anonymously on the internet. As part of its offerings, Tor provides hidden services, specifically anonymous networking between servers that are configured to receive inbound connections only through Tor. In order to route requests to these hidden services, a namespace is used to identify the resolution requests to such services. Tor uses the .onion namespace under a non-delegated (pseudo) top-level-domain. Although the Tor system was designed to prevent .onion requests from leaking into the global DNS resolution process, numerous requests are still observed in the global DNS, causing concern about the severity of the leakage and the exposure of sensitive private data.