Launch of Verisign’s First IDN New gTLD, .コム
Guest post from Manish Dalal, Vice President, Verisign Naming Services Asia
The composition of the Internet’s population continues to evolve toward a more localized Web. Asia has been leading the way forward as the populations in that region come online and begin creating and consuming content in their local languages. According to Internet World Stats, over 48 percent of all Internet users are located in Asia and, according to W3Techs, approximately 45 percent of all websites in the world are in a language other than English.
Still, navigation of the Internet through a URL is primarily in English. Therefore, by enabling more end users to navigate the Internet in scripts representing their native language, and giving more companies the ability to maintain a common brand identity across many scripts, Internationalized Domain Names (IDNs) have the potential to make the Internet more accessible and thus more usable to end users around the world. This accessibility is why IDNs have generated considerable attention since Verisign introduced IDNs at the second-level in 2000.

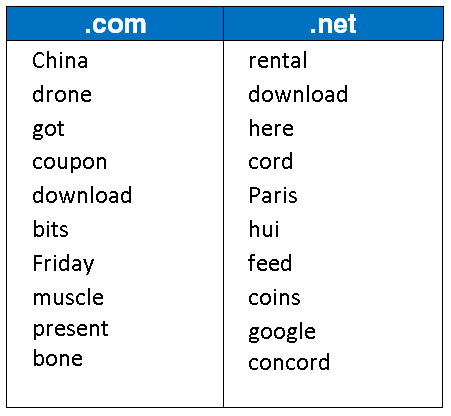
Top 10 Trending Keywords in .Com & .Net Registrations in November

In Network Security Design, It’s About the Users
One of the longstanding goals of network security design is to be able to prove that a system – any system – is secure.
Designers would like to be able to show that a system, properly implemented and operated, meets its objectives for confidentiality, integrity, availability and other attributes against the variety of threats the system may encounter.
A half century into the computing revolution, this goal remains elusive.
One reason for the shortcoming is theoretical: Computer scientists have made limited progress in proving lower bounds for the difficulty of solving the specific mathematical problems underlying most of today’s cryptography. Although those problems are widely believed to be hard, there’s no assurance that they must be so – and indeed it turns out that some of them may be quite easy to solve given the availability of a full-scale quantum computer.
Another reason is a quite practical one: Even given building blocks that offer a high level of security, designers, as well as implementers, may well put them together in unexpected ways that ultimately undermine the very goals they were supposed to achieve.

As WHOIS Transitions to RDAP, How Do We Avoid the Same Mistakes?
In 1905, philosopher George Santayana famously noted, “Those who cannot remember the past are condemned to repeat it.” When past attempts to resolve a challenge have failed, it makes sense to consider different approaches even if they seem controversial or otherwise at odds with maintaining the status quo. Such is the case with the opportunity to make real progress in addressing the many functional issues associated with WHOIS. We need to think differently.

How DANE Strengthens Security for TLS, S/MIME and Other Applications
The Domain Name System (DNS) offers ways to significantly strengthen the security of Internet applications via a new protocol called the DNS-based Authentication of Named Entities (DANE). One problem it helps to solve is how to easily find keys for end users and systems in a secure and scalable manner. It can also help to address well-known vulnerabilities in the public Certification Authority (CA) model. Applications today need to trust a large number of global CAs. There are no scoping or naming constraints for these CAs – each one can issue certificates for any server or client on the Internet, so the weakest CA can compromise the security of the whole system. As described later in this article, DANE can address this vulnerability.

3 Tips for Improving Your Website DNS Performance During the Holidays
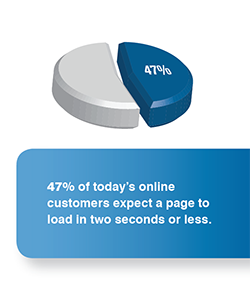
For consumers who are increasingly impatient and expect a website to load within two seconds or less, the majority will quickly abandon a slow-loading page along with their shopping cart, resulting in lost revenue. With so many potential problems to slow down your site, the domain name system (DNS) doesn’t have to be one of them.
What is DNS?
DNS is the Internet’s equivalent to a phone book. It maintains a directory of domain names and translates them to their respective Internet Protocol (IP) addresses, enabling the end user to access a desired Web page. Any disruption to the DNS during the holiday season can be disastrous for retailers.
“DNS is the Achilles’ heel of the Web, often forgotten, and its impact on website performance is ignored until it breaks down,” explains Mehdi Daoudi, CEO of Web performance monitoring firm Catchpoint. However, it doesn’t have to be.

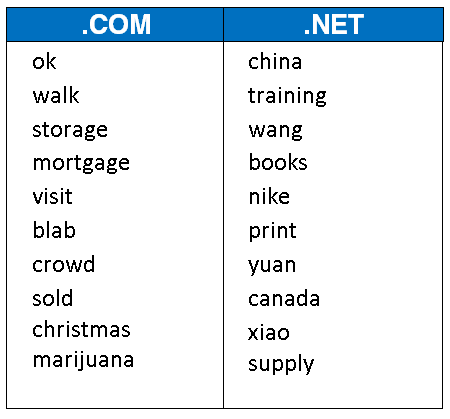
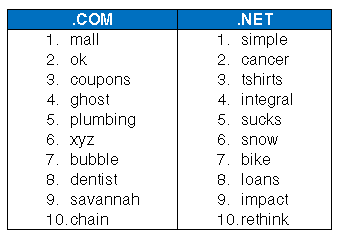
Top 10 Trending Keywords in .Com & .Net Registrations in October

Verisign DDoS Trends Report: Verisign Mitigates More Attack Activity in Q3 2015 Than Any Other Quarter During Last Two Years

Protect Your Privacy: Opt Out of Public DNS Data Collection
This blog was initially published on Oct. 23, 2015. On Nov. 2, 2020, Neustar announced the acquisition of Verisign’s Public DNS. Further information can be found here.
We’ve all seen the check boxes. They’re hidden at the bottom of webpages. You can’t ignore them, but sometimes you forget they are there. They offer to send you deals and coupons. Some even offer to connect you with their partners for similar benefits. Do you check the box?
In these situations you are given a choice of how you want your personal information used. These sites provide the option to trade some of your personal information for a future benefit. If you decide to opt in, your personal information will be transferred, traded or sold to others, and in exchange you will receive something in return, i.e., 10 percent off your next purchase, advance notice of upcoming events, a free gift, etc. If you opt out, you will receive nothing. Regardless of the return, you were given a choice; opt in and receive a benefit for the use of your personal information, or opt out and be content that your personal information won’t be sold.