Defense in Depth — Protect Your Organization at the DNS Layer with DNS Firewall
A comprehensive defense-in-depth strategy requires security mechanisms to be applied through the implementation of hardware, software and security policies. Hardware protection includes, but is not limited to, the implementation of next generation firewalls (NGFW), intrusion prevention systems/intrusion detection systems (IPS/IDS) and secure Web gateways (SWG). Software-based protection is done through anti-virus software deployments, automated patch management or tools for Internet monitoring. Finally, no defense-in-depth strategy would be complete without the implementation of strong security policies that prescribe processes for incident reporting, service and system audits, and security awareness training.

4 Steps to Build Your Personal Brand Online
If you are a recent grad or someone looking to make a career move, make sure to think about your presence on the internet. Last year, 92 percent of recruiters used social media in the recruiting process. If a hiring manager looked you up online, what would he or she find? You can give yourself that extra edge and stand out from the crowd by taking control of your digital footprint. And, the easiest way to do that? Register a domain name and secure your professional space online to show who you are and what you can offer. In fact, 56 percent of all hiring managers are more impressed by a candidate’s personal website than any other personal branding tool.

Verisign Champions Cybersecurity Awareness in October
 Cybersecurity is no longer a concern for just IT and security professionals. Recent breaches at organizations like Sony, Target, JP Morgan Chase, and numerous U.S. government entities have brought the issue of cyber-attacks very close to home. If you bank online, use your debit card at a local store or engage in any activity that relies on an Internet-connected system, you are at risk.
Cybersecurity is no longer a concern for just IT and security professionals. Recent breaches at organizations like Sony, Target, JP Morgan Chase, and numerous U.S. government entities have brought the issue of cyber-attacks very close to home. If you bank online, use your debit card at a local store or engage in any activity that relies on an Internet-connected system, you are at risk.

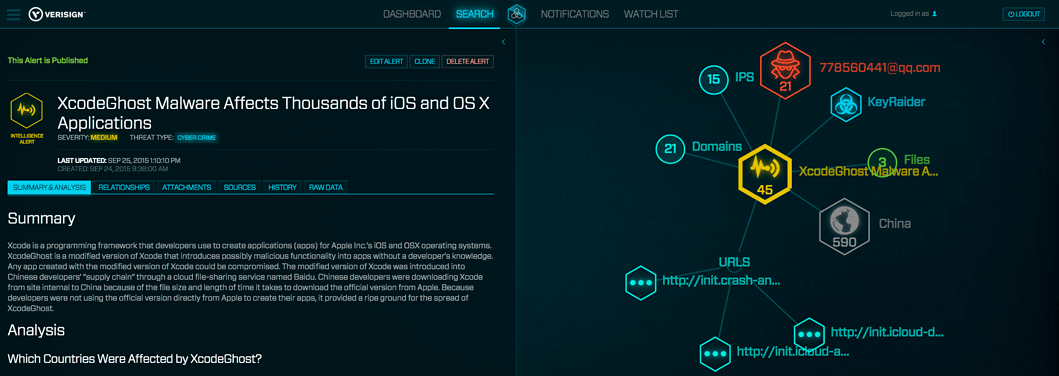
Verisign iDefense Analysis of XcodeGhost
Background

Verisign 2015 Online Survey: 97 Percent of SMBs Would Recommend Having a Website to Other SMBs
Almost three-quarters of Americans go online at least once a day. If you are a small business looking to grow, you need to go where your customers are. That means getting your business online with a domain name – whether it’s with branded email, a web address for your social media page, or a business website.
In September 2015, Verisign conducted a survey of 787 U.S. internet consumers aged 18 to 59 and 456 U.S. small businesses to learn more about their online behaviors and preferences – focusing on how consumers use the internet and the benefits of an online presence for a business.

Thinking Ahead on Privacy in the Domain Name System
Earlier this year, I wrote about a recent enhancement to privacy in the Domain Name System (DNS) called qname-minimization. Following the principle of minimum disclosure, this enhancement reduces the information content of a DNS query to the minimum necessary to get either an authoritative response from a name server, or a referral to another name server. This is some additional text.
In typical DNS deployments, queries sent to an authoritative name server originate at a recursive name server that acts on behalf of a community of users, for instance, employees at a company or subscribers at an Internet Service Provider (ISP). A recursive name server maintains a cache of previous responses, and only sends queries to an authoritative name server when it doesn’t have a recent response in its cache. As a result, DNS query traffic from a recursive name server to an authoritative name server corresponds to samples of a community’s browsing patterns. Therefore, qname-minimization may be an adequate starting point to address privacy concerns for these exchanges, both in terms of information available to outside parties and to the authoritative name server.

Highlights From vBSDcon: Plenary Talk Videos Now Available
vBSDcon, hosted by Verisign, brought more than 100 attendees from the Berkeley Software Distribution (BSD) community together for a series of plenary talks, educational sessions and networking opportunities earlier this month.
“This biennial conference has been particularly special to us because of the grassroots effort within Verisign to be sure we do our part to help advance BSD,” said Verisign CTO Burt Kaliski.
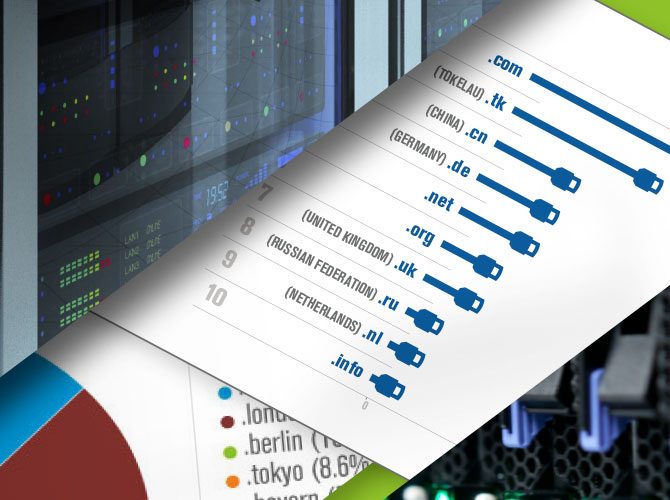
Internet Grows to 296 Million Domain Names in Second Quarter of 2015

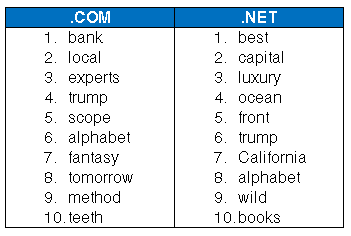
Top 10 Trending Keywords in .com & .net Registrations in August

Protect Your Network from BYOD Malware Threats with the Verisign DNS Firewall
Today’s new age of ubiquitous connectivity has created an insatiable and growing demand among employees and consumers to be online with familiar systems and tools at all times. Employees are no longer satisfied with the limited choices in devices and tools provided to them by their corporate IT organizations. They want to use what they want,when they want. They believe that choosing their own devices and tools provides them with the highest level of comfort and efficiency. This desire to use personal devices in work environments, referred to as “bring your own device (BYOD),” coupled with the growing cyber-attack surface, poses significant challenges to IT organizations. These challenges are leading such organizations to ask themselves – Are we ready to support BYOD?