Verisign Announces Third Round of #InternetOfficial Contest First Prize Winners
We’re excited to announce the third – and final – round of our monthly #InternetOfficial contest First Prize Winners!
This round of winners brings the total number of First Prize Winners to 15. Each will receive $5,000, and is eligible to compete to win the #InternetOfficial contest grand prize of $30,000 (the First Prize Winners who submit a video will proceed to the final round for an opportunity to win the grand prize).
Our distinguished panel of top industry experts and celebrity judges has determined the five best .com domain names entered into the #InternetOfficial contest during the third monthly entry period.

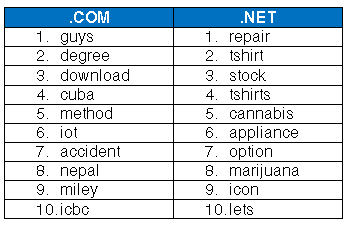
Top 10 Trending Keywords in .Com & .Net Registrations in May
The top 10 trending keywords registered in .com and .net during the month of May 2015 are below. Any surprises?
Click here to see other domain trends blog posts and make sure you check back on the second Tuesday of each month to see the latest keyword registration trends in .com and .net. Better yet, subscribe to Verisign Blog to have the posts delivered directly to your inbox.
If you’d like to do your own domain name keyword research, check out Verisign Domain View, a tool that allows you to enter keywords to see registration trends in .com and .net.
Note: Each list was developed by examining keyword registration growth relative to the preceding month, such that those keywords with the highest percentage of registration growth are being reported on. This method is used to eliminate commonly registered keywords such as “online” and “shop” to provide a true look at monthly trends.

3 Key Steps for SMBs to Protect Their Website and Critical Internet Services
The National Small Business Association (NBSA) recently released a report revealing that half of all small businesses have been the victim of a cyber-attack – and the cost of dealing with these attacks has skyrocketed to $20,752 per attack. In about a third of attacks, the victim’s website was taken down, often for days. The impact of such outages cannot be measured by the immediate lost revenue alone, as the long term impact of the harm to your reputation and customer loss cannot be easily calculated.

How Will Your Registration Data Be Managed in the Future?
Benjamin Franklin once said, “By failing to prepare, you are preparing to fail.” As we consider how Internet domain and address registration data is managed and accessed in a post-WHOIS era, and given the long history of failure in addressing the shortcomings of WHOIS, it is extremely important to start preparing now for the eventual replacement of WHOIS. This is the fundamental purpose of the next Registration Operations Workshop (ROW) that is scheduled for Sunday, July 19, 2015, in Prague, Czech Republic.
ROW 2015-2 will take place at the Hilton Prague hotel, the same venue as the 93rd meeting of the Internet Engineering Task Force (IETF-93). The workshop will be dedicated to discussion and planning for development and testing deployments of the Registration Data Access Protocol (RDAP), a recent work product of the IETF that is documented in Request For Comments (RFC) documents 7480, 7481, 7482, 7483, and 7484. RDAP was designed from the beginning to address the many shortcomings of WHOIS, but we have very little experience with early-stage implementations that can be used to inform the policy decisions that need to be made. Additional information about WHOIS and RDAP can be found in my “Where Do Old Protocols Go To Die?” blog post published earlier this year. (more…)

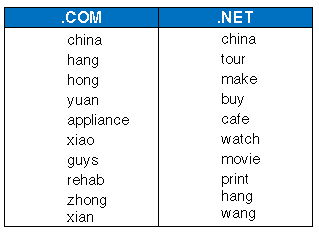
Top 10 Trending Keywords in .Com & .Net Registrations in April

Verisign Announces Second Round of #InternetOfficial Contest First Prize Winners
To help celebrate National Small Business Week, today we’re excited to announce the second round of our #InternetOfficial contest First Prize Winners!
As we previously noted on our blog, up to 15 monthly First Prize Winners will receive $5,000 each, and are eligible to compete to win the #InternetOfficial contest grand prize of $30,000 (the First Prize Winners who submit a video will proceed to the final round for an opportunity to win the grand prize).
Our renowned panel of top industry experts and celebrity judges has determined the five best .com domain names entered into the #InternetOfficial contest during the second monthly entry period.

Save the Date: Verisign to host vBSDCon, Sept. 11-13, 2015
Verisign is excited to announce that we are hosting the second vBSDcon event, taking place Sept. 11-13, 2015, at the Sheraton hotel in Reston, Va. We welcome all members of the various Berkeley Software Distribution (BSD) communities, such as FreeBSD, OpenBSD, NetBSD and others, to join us for a series of plenary talks, Birds of a Feather (BoF) discussions, educational sessions and best practice conversations, as well as the opportunity to network with one another in person.

Verisign Announces First Round of #InternetOfficial Contest First Prize Winners
The results are in and today we’re excited to announce the first round of monthly First Prize Winners from our #InternetOfficial contest celebrating #30YearsofCOM!
Our First Prize Winners will receive $5,000 each, and are eligible to compete to win the #InternetOfficial contest grand prize of $30,000.
As we previously noted on our blog, the #InternetOfficial contest, which is open to U.S. residents only, will feature up to five monthly First Prize Winners during the contest’s entry period (for a total of up to 15 monthly First Prize Winners) and one Grand Prize Winner. Each First Prize Winner will receive $5,000 and the opportunity to submit a video explaining the beauty of their entry. The First Prize Winners who submit a video will proceed to the final round for an opportunity to win the grand prize.
Our illustrious panel of top industry experts and celebrity judges has determined the five best .com domain names entered into the #InternetOfficial contest during the first monthly entry period.

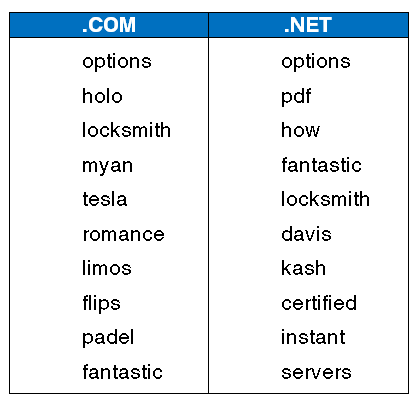
Top 10 Trending Keywords in .Com & .Net Registrations in March

Verisign OpenHybrid™ for Corero and Amazon Web Services Now Available
Verisign outlined its vision for a revolutionary new approach to Distributed Denial of Service (DDoS) protection by announcing the availability of the Verisign OpenHybrid™ architecture, which helps organizations protect their critical assets and applications across distributed environments from DDoS attacks, using a single solution. By integrating intelligence from a customer’s existing security defenses, Verisign OpenHybrid™ provides timely detection and restoration of services in the event of an attack, while providing increased visibility of DDoS threats across multiple environments such as private datacenters and public clouds.
In an earlier blog post on the topic, I noted the increasing scale and complexity of DDoS attacks, and the strong need for organizations to enable awareness and mitigation of attacks across on-premise devices, in addition to both public and private cloud environments using standards based open protocols.
Today we are pleased to announce two important updates in our path toward enabling open DDoS protection: the availability of Verisign OpenHybrid™ for Corero SmartWall TDS and Verisign OpenHybrid™ for customers hosted in the Amazon Web Services Elastic Compute Cloud.