
Is it Time for a Registration Operations Industry Association? Part III
In Parts I and II of this series of blog posts I described the need for a registration operations industry association. At the end of Part II, I wrote that Part III will describe “an opportunity for everyone that’s interested in discussing this topic in a live environment.” The large number of people attending ICANN 51 in Los Angeles presents the best chance of discussion with many potential participants being in the same place at the same time. Let’s take advantage of that proximity.
Verisign will host a workshop for all interested people during the week of ICANN 51. The event will be held at the Hyatt Regency Century Plaza hotel (the same venue for ICANN 51, though this event is not affiliated with ICANN) on the morning of Thursday, October 16, 2014, to discuss the challenges of registration technical operations and to explore ways to address those challenges. We’ve set up a website at www.regiops.net to provide information, describe the event, and allow people to register. We’re asking people to register in advance so we can make sure that we have a large enough room reserved and that we provide enough food for breakfast and lunch.

Make Your Idea Internet Official: Your .com Is Waiting
As you think about bringing your business online, look no further than .com, one of the most universally recognized domains on the internet. While .com is highly desirable for the businesses and individuals around the globe, did you know there are still millions upon millions of great .com domain names available for registration? Let’s take a look at the latest facts around .com availability, based on an analysis of .com domain name registrations as of July 2014:
- 23 million times a day, a .com domain name availability check is successful [1]
- Over 95 percent of five-character .com combinations are available
- More than 99 percent of six-character .com combinations are available

Is it Time for a Registration Operations Industry Association? Part II
In Part I of this series of blog posts I described the need for an industry association of operators to discuss the technical tasks, such as the development, deployment, and ongoing systems administration of the Extensible Provisioning Protocol (EPP), performed by registries and registrars to ensure interoperability and share best practices when providing registration services. In this blog post I’ll describe a way to make that happen.
I’ve spoken to a number of registrars who have described the challenges they face in implementing the many different EPP extensions being developed by registry operators. Here’s a concrete example: the Net::DRI Perl implementation of an EPP client includes contact extensions for 24 different registries. A registrar that wishes to manage contacts with those registries needs to implement a contact extension for each one! With the addition of new gTLDs and many new registry operators with new business models the number of extensions can only increase. How would an industry association address these challenges and reduce confusion for everyone? How could an association be structured?

Is it Time for a Registration Operations Industry Association?
Since 2001 there have been occasional conversations on technical mailing lists exploring the concept of creating an independent industry association or consortium of domain registration operators. My recent experiences with the evolution of extensions to the Extensible Provisioning Protocol (EPP) have convinced me to look at these suggestions more closely, and I’m now convinced that this is an idea worth exploring.
“Registration Operations” refers to the technical tasks, such as the development, deployment, and ongoing systems administration of EPP, performed by registries and registrars to provide registration services. While EPP is used to provide domain name registration and management services, registration operations also include the tasks performed by Regional Internet Registries (RIRs) to provide address registration and systems administration services.

Why the UK needs a Go and Grow Online campaign
Guest Post from Emma Jones, founder of UK-based Enterprise Nation
With almost 50% of small businesses said to be without a website and, of those that are online, only a few taking the opportunity to trade, Emma Jones of London-based small business network, Enterprise Nation, outlines the need for a campaign to help British businesses make the most of the web.
When I founded Enterprise Nation in 2005 it was to help people turn their good ideas into great businesses. Now, by offering expert advice, events, networking and inspiring books, we have more than 60,000 members in the UK who are all looking to create thriving small businesses.
When Enterprise Nation first started, Facebook was still in its infancy and Twitter hadn’t even been founded, which shows just how quickly the online world has changed! With over 2 billion people now online across the globe, the digital world represents a big opportunity for small businesses. Having a website to showcase your products and services is like having a shop window that the world can see into, at any time of the day (or night!). It’s never been so easy to launch online with template website providers, blogging platforms and social media. So why is it that so many businesses are yet to embrace the web and reap the rewards?

Verisign Mitigates 300 Gbps DDoS Attack and Other Q2 2014 DDoS Trends
It has been another busy quarter for the team that works on our DDoS Protection Services here at Verisign. As detailed in the recent release of our Q2 2014 DDoS Trends Report, from April to June of this year, we not only saw a jump in frequency and size of attacks against our customers, we witnessed the largest DDoS attack we’ve ever observed and mitigated – an attack over 300 Gbps against one of our Media and Entertainment customers.

Website Usage Analysis in the New gTLDs
A recent study, by EURid and the Leuven Statistics Research Centre, set out to better understand the most common usage of websites that are linked to domains, and we thought it would be an interesting exercise to extend similar analysis to the new generic top-level domain (gTLD) market. So, we analyzed all second-level domains registered in new gTLDs according to published zone files on June 29, 2014. Verisign utilizes our own proprietary process for classifying websites, which results in similar classifications to those by EURid. The primary difference is that the Verisign classification method is machine-based and is evaluated for each domain independently, while the EURid approach leveraged samples that humans classified.
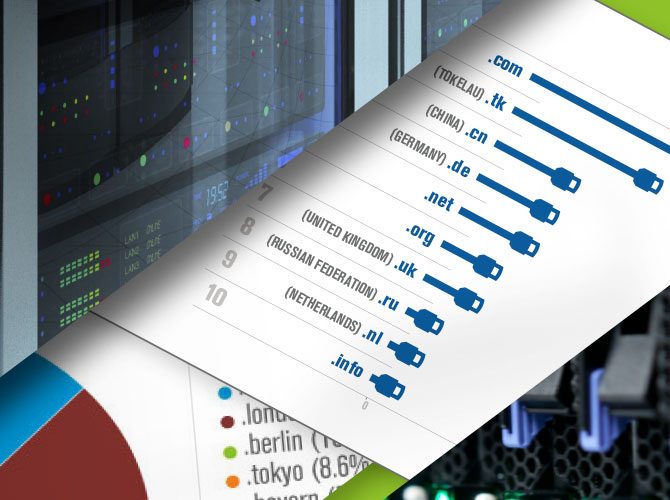
Internet Grows to 276 Million Domain Names in the First Quarter of 2014
Today, we released the latest issue of the Domain Name Industry Brief, which showed the internet grew by five million domain names in the first quarter of 2014. The total number of domain names across all top-level domains (TLDs) is now 276 million! This is a 1.7 percent increase over the fourth quarter of 2013. [1]

UK Small Businesses to Benefit From Go and Grow Online Initiative
Verisign is proud to announce that we are a sponsor of Enterprise Nation’s Go and Grow Online initiative that aims to encourage more businesses in the UK to get online and support existing online businesses to grow their online presence.

New from Verisign Labs – Measuring Privacy Disclosures in URL Query Strings
http://www.example.com/path/submit.php?user=userabc&pageid=012345&utm_referrer=rss&localtime=+0500
In your personal experience, as in our example, you might have realized that the URL was as much about you, the client, as it was about the web resource you were trying to access. Indeed, internet addresses may contain a wealth of information about the identities and activities of the users visiting them. URLs often utilize query strings (i.e., key-value pairs appended to the URL path; in our example, everything after the question mark) as a means to pass session parameters and form data. While sometimes benign and necessary to render the web page, query strings often contain tracking mechanisms, user names, email addresses and other information that users may not wish to publicly reveal. In isolation this is not particularly problematic, but the growth of web 2.0 platforms such as social networks and micro-blogging means such URLs are increasingly being publicly broadcast.