Verisign just released its Q1 2018 DDoS Trends Report, which represents a unique view into the attack trends unfolding online, through observations and insights derived from distributed denial of service (DDoS) attack mitigations enacted on behalf of Verisign DDoS Protection Services, and security research conducted by Verisign Security Services.

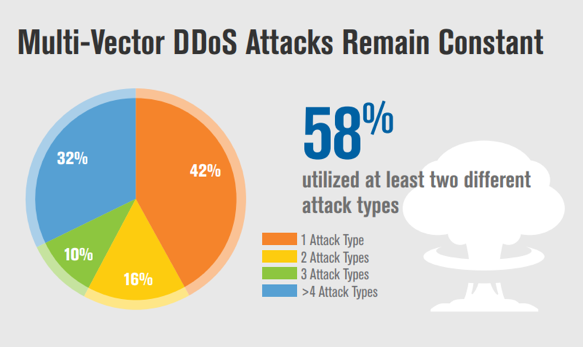
Verisign observed that 58 percent of DDoS attacks that were mitigated in Q1 2018 employed multiple attack types. There was a 53 percent increase in the number of attacks, as well as a 47 percent increase in the attack peak sizes, when compared to Q4 2017; however, the attack peak sizes have decreased by 21 percent, year over year.
The largest volumetric and highest intensity DDoS attack observed by Verisign in Q1 2018 was a multi-vector attack that peaked at approximately 70 Gigabits per second (Gbps) and 7.4 Million packets per second (Mpps). The attack consisted of a wide range of attack vectors including TCP SYN and TCP RST floods, DNS and SNMP amplification attacks, Internet Control Message Protocol (ICMP) floods, and invalid packets.
Key DDoS Trends and Observations:
- Fifty percent of DDoS attacks were User Datagram Protocol (UDP) floods.
- TCP-based attacks were the second most common attack vector, making up 26 percent of attack types in the quarter.
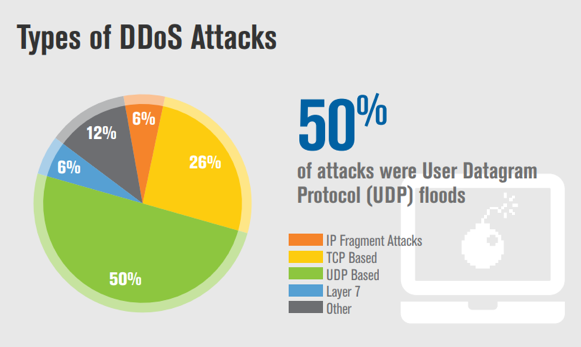
- Fifty-eight percent of DDoS attacks mitigated by Verisign in Q1 2018 employed multiple attack types.
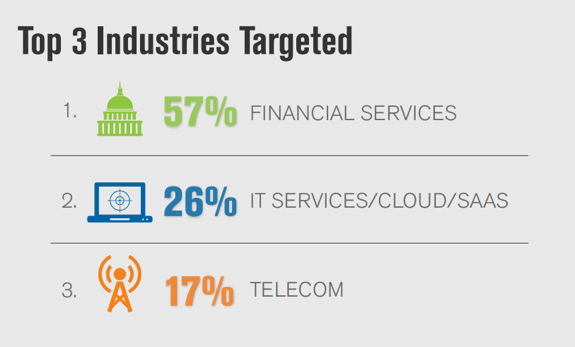
- The Financial industry, representing 57 percent of mitigation activity, was the most frequently targeted industry for Q1 2018. The IT/Cloud/SaaS industry experienced the second highest number of DDoS attacks, representing 26 percent of mitigation activity, followed by the Telecom industry, representing 17 percent of mitigation activity.
Selecting the Right DDoS Mitigation Strategy for Your Organization
As DDoS attacks remain a viable and unpredictable threat, how does your company determine the best mitigation strategy (or strategies) for protecting your online assets? What are your downtime tolerances? Whatever your organization’s downtime tolerance, staff readiness, and technical expertise, selecting a DDoS solution that accommodates a variety of mitigation strategies is paramount to getting the protection— and value—you deserve.
Read the report to learn more about DDoS mitigation strategies.
For more DDoS Trends in Q1 2018, download the full report, and be sure to check back in a few months when we release our Q2 2018 DDoS Trends Report.



1 comment
Comments are closed.