Verisign just released its Q3 2016 DDoS Trends Report, which provides a unique view into online distributed denial of service (DDoS) attack trends from mitigations enacted on behalf of Verisign DDoS Protection Services and research conducted by Verisign iDefense Security Intelligence Services.
User Datagram Protocol (UDP) flood attacks continue to dominate in Q3 2016, making up 49 percent of the total attacks in the quarter. The most common UDP flood attacks mitigated were Domain Name System (DNS) reflection attacks, followed by Network Time Protocol (NTP) reflection attacks.
The highest intensity flood attack in Q3 2016 was a TCP SYN flood that peaked at approximately 60 Gigabits per second (Gbps) and 150 Million packets per second (Mpps). This flood attack is one of the highest packets per second attacks ever observed by Verisign, surpassing the previous flood of 125 Mpps mitigated by Verisign in Q4 2015.
The largest attack in Q3 2016 utilized the Generic Routing Encapsulation (GRE) protocol (IP protocol 47) and peaked at 250+ Gbps and 50+ Mpps. This is the first time Verisign observed this type of attack against our customer base.
Other key trends and observations include:
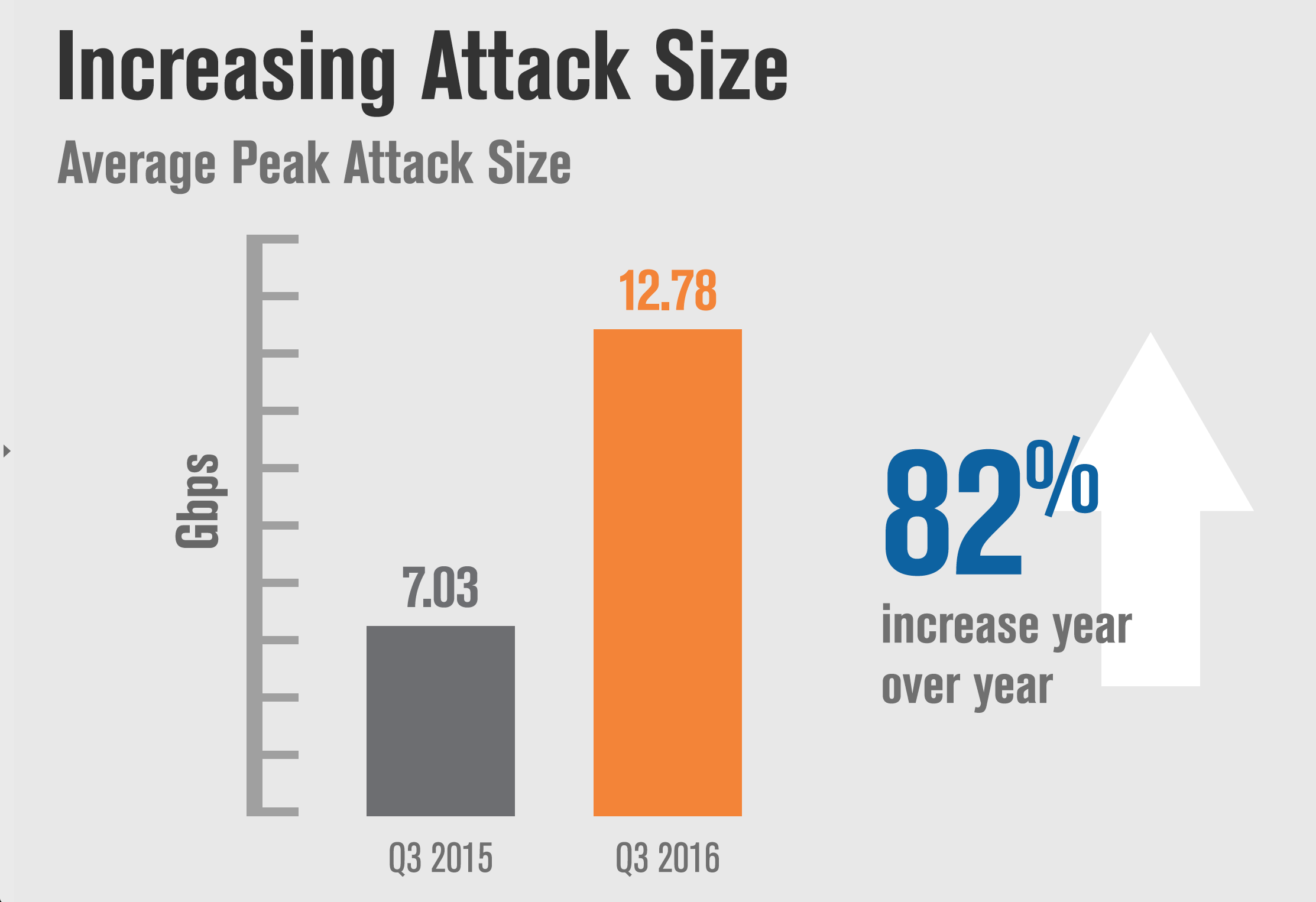
- Average peak attack sizes in 2016 continued to trend larger than in previously recorded years. The average peak attack size in Q3 2016 was 12.78 Gbps, an 82 percent increase year over year.
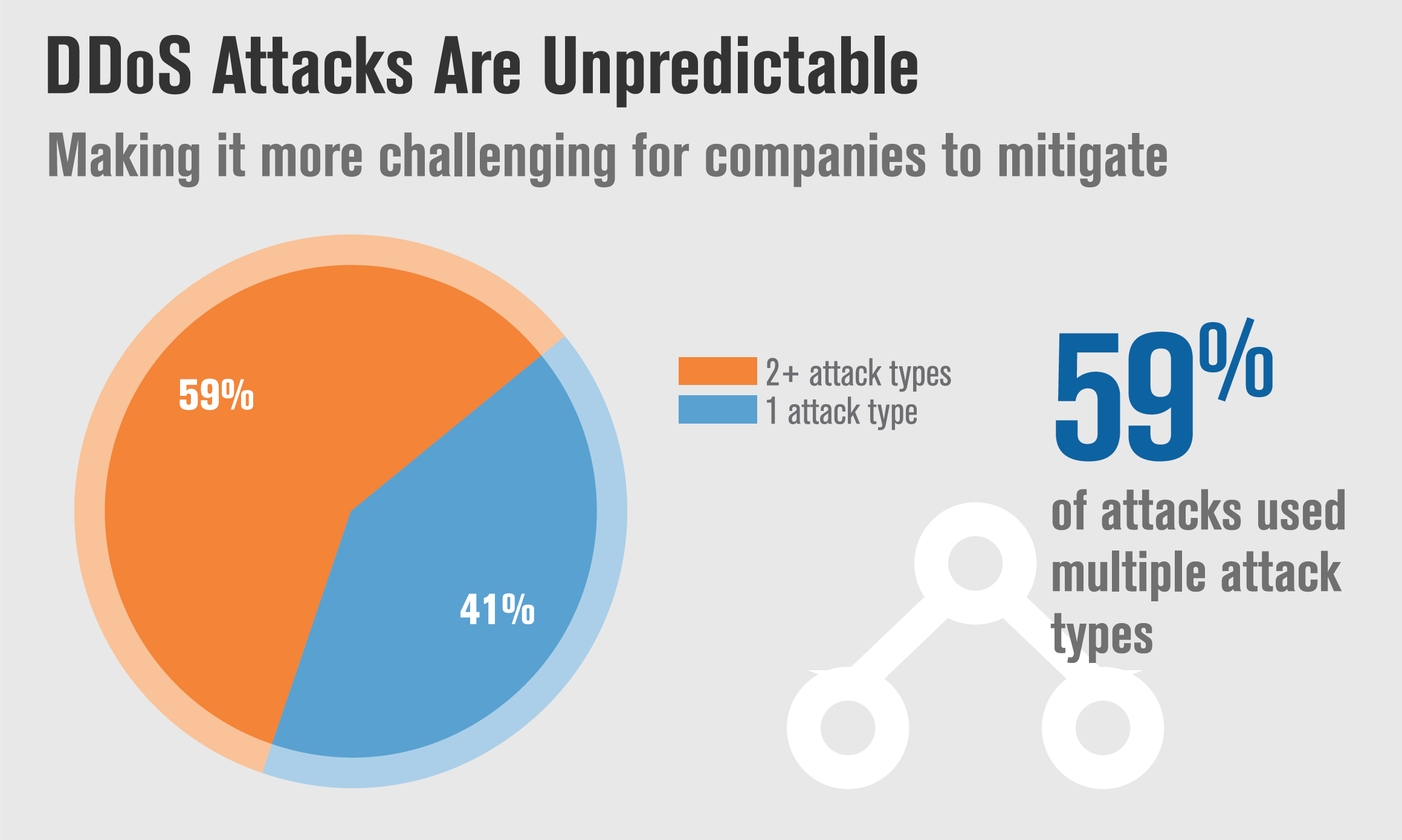
- Fifty-nine percent of the DDoS attacks utilized two or more different attack types.
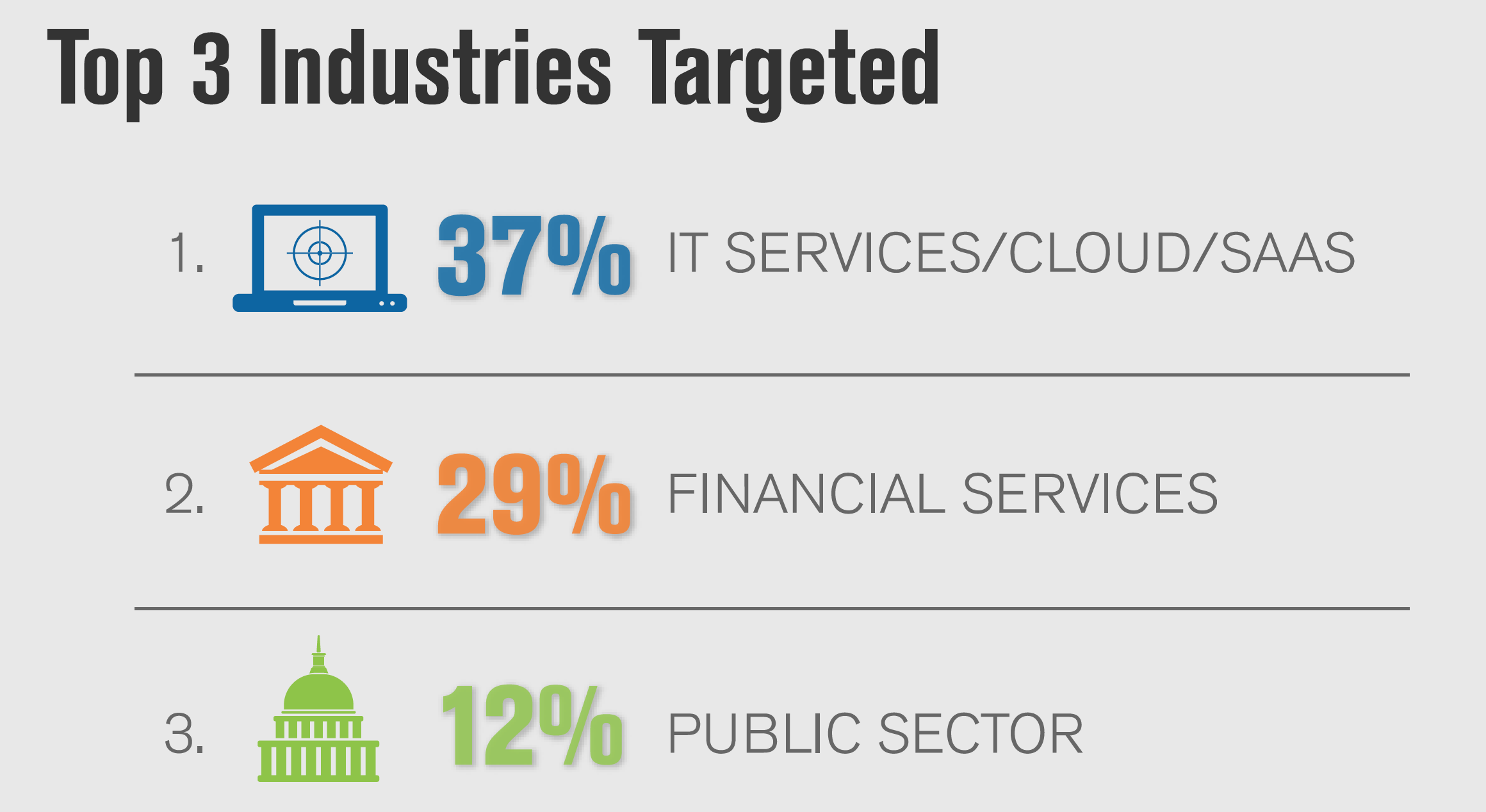
- IT Services/Cloud/SaaS, representing 37 percent of mitigation activity, remains the most frequently targeted industry for the eighth consecutive quarter, closely followed by the Financial industry, representing 29 percent of all mitigations.
For more DDoS trends in Q3 2016, download the full report, and be sure to check back in a few months when we release our Q4 2016 DDoS Trends Report.




It is also called the Layer 7 attack as the vulnerability is found in the Application Layer of the TCP/IP. The article is good. It gave a lot of information.