Two principles in computer security that help bound the impact of a security compromise are the principle of least privilege and the principle of minimum disclosure or need-to-know.
As described by Jerome Saltzer in a July 1974 Communications of the ACM article, Protection and the Control of Information Sharing in Multics, the principle of least privilege states, “Every program and every privileged user should operate using the least amount of privilege necessary to complete the job.”
Need-to-know is the counterpart for sharing information: a system component should be given just enough information to perform its role, and no more. The US Department of Health and Human services adopts this principle in the HIPAA privacy policy, for example, which states: “protected health information should not be used or disclosed when it is not necessary to satisfy a particular purpose or carry out a function.”
There may be tradeoffs, of course, between minimizing the amount of privilege or information given to a component in a system, and other objectives such as performance or simplicity. For instance, a component may be able to do its job more efficiently if given more than the minimum amount. And it may be easier just to share more than is needed, than to extract out just the minimum required. The minimum amounts of privilege may also be hard to determine exactly, and they might change over time as the system evolves or if it is used in new ways.
Least privilege is well established in DNS through the delegation from one name server to another of just the authority it needs to handle requests within a specific subdomain. The principle of minimum disclosure has come to the forefront recently in the form of a technique called qname-minimization, which aims to improve privacy in the Domain Name System (DNS).
(more…)

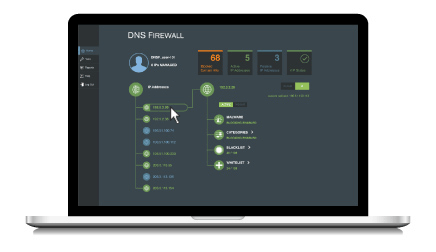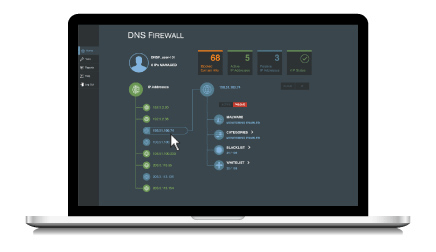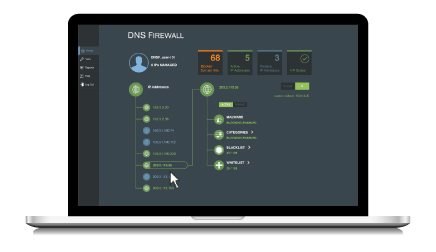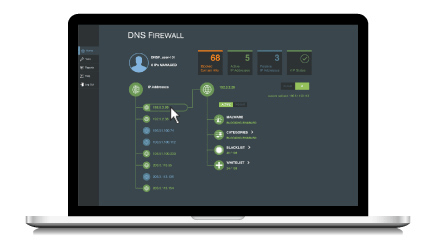



 A network traffic analyzer can tell you what’s happening in your network, while a Domain Name System (DNS) analyzer can provide context on the “why” and “how.”
A network traffic analyzer can tell you what’s happening in your network, while a Domain Name System (DNS) analyzer can provide context on the “why” and “how.” 

