Defending against cyber threats is not only critical, but increasingly difficult and expensive. Just a quick glance at today’s news headlines and it is clear that these threats present numerous challenges to Internet users and the organizations that both serve and employ them. For example, in 2014, McAfee Labs observed a 75 percent year-over-year increase in new malware equating to 387 new threats per minute. Further, the Ponemon Institute estimates the average data breach costs large organizations $3.8 million per event.
Most solutions either require extensive investment or do not meet an organization’s constantly evolving needs. Traditional, appliance-based security solutions can require organizations to shell out considerable amounts of money, both in up-front capital expenditure and in on-going maintenance fees. Conversely, many managed cloud-based offerings do not provide the critical capability to customize the solution based on an organization’s specific business environment and security needs. Finally, do-it-yourself (DIY) open-source solutions suffer from constant patching and maintenance problems.
Enter the Verisign DNS Firewall, an easy-to-configure, cost effective managed cloud-based service that offers robust protection from unwanted content, malware and advanced persistent threats (APTs), delivered with the ability to customize filtering to suit an organization’s unique needs.
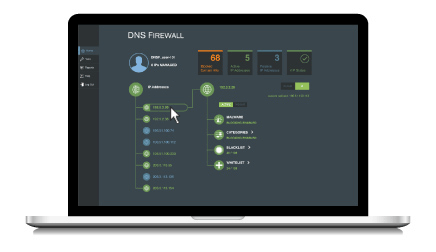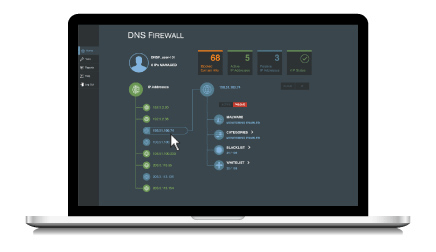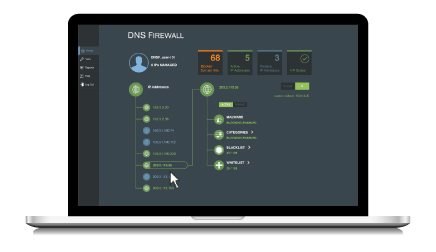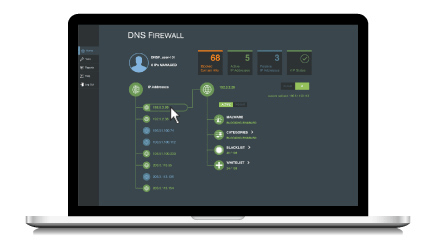



 A network traffic analyzer can tell you what’s happening in your network, while a Domain Name System (DNS) analyzer can provide context on the “why” and “how.”
A network traffic analyzer can tell you what’s happening in your network, while a Domain Name System (DNS) analyzer can provide context on the “why” and “how.” 


